 |
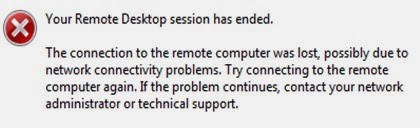
| Your Remote Desktop sessions has ended. The connection to the remote computer was lost, possibly due to network connectivity problems. Try connecting to the remote computer again. If the problem continues, contact your network administrator or technical support |
Of course, you would think 'orphaned session' or a terminal server setting, but that was not the case. No limits were set and I could see the users' sessions disconnecting just fine from the server. The first connection would work fine until the user logged off the terminal server or was disconnected. Once that happened, the user could not sign in again with the above error.
But here's the trick: If I rebooted the server or the firewall at the location, the users could connect again - but again, only once, then another reboot would be required.
So after confirming the usual suspects like DNS, AD account status, and VPN tunnels were all active and working normally, I decided the issue had to be something deeper. I found the following error in the Terminal Server's System Event Log:
 |
| "Event 56, TermDD - The Terminal Server security layer detected an error in the protocol stream and has disconnected the client." |
This little Event ID led down a real rabbit-hole of blog posts, forum discussions, and random Microsoft KB articles. Let me give you some of the highlights:
- Reduce the encryption level of the terminal server to Low & use "RDP Encryption"
- Set the RDP encryption algorithm to balance network & memory usage
- Enable 'keep alive' on the terminal server
- Disable TCP Chimney Offload, Receive-Side Scaling State (RSS), and NetDMA
- Confirm RDC client version is the latest on all clients
- Use "ERR.EXE" to analyze the last word byte of the above error (B50000D0 in this case)
 |
| "Dissector bug, protocol T.124 proto.c:3478 failed assertion (guint)hfindex < gpa_hfinfo.len) unregistered hf!" |
I was still not convinced that the Sonicwall at the location wasn't to blame for all this. After all, we had other network issues with a business application at that same location which had still not been fixed.
Bruised and beaten, I elected to open support tickets with Sonicwall and Microsoft and begin working this issue from each end with them....
(To be continued...)
No comments:
Post a Comment